Risk Management
Information Risk Management
Policies and Basic Approach
Mitsui & Co. declared "Information Technology (IT) policy" as a basic policy for IT utilization to promote further awareness raising of employees and enhancement of IT governance.
Information Security Policy
- Approach toward Information Security
Mitsui recognizes the importance of information security, and shall implement appropriate management of information assets, including information and ICT assets, for the purpose of timely and effective use of information in compliance with "Mitsui & Co., Ltd. Corporate Governance and Internal Control Principles", while striving to continuously improve such management on a global and group-wide basis. - Compliance with Regulations (Establishing Compliance)
Mitsui shall comply with regulations, established standards, and other codes related to information security, and shall work towards the establishment and maintenance of compliant and suitable information security. - Protection of Information Assets
Mitsui shall implement appropriate management for ensuring the confidentiality, integrity and availability of information assets, and work to protect its information assets from all possible threats. - Response to Accidents
While working to prevent the occurrence of any accidents related to information security, in the unlikely event of an accident, Mitsui shall promptly take appropriate response measures including preventative steps against the reoccurrence of such an accident.
Effective from September, 2005
Amended on October, 2013
Kenichi Hori
President and Chief Executive Officer
Goals and Targets
Targets and Progress
| Goals and Targets | Performance Indices | Results for FY March 2025 |
|---|---|---|
| Designate significant affiliates for cybersecurity every year and monitor the state of compliance with the Mitsui & Co. Group Cybersecurity Standards | Compliance rate | 80% |
Sustainability Governance and Oversight
The important principles for our global group information strategy are formulated in line with the corporate management policy through the discussions at the Information Strategy Committee, as an advisory body under the control of the Executive Committee, which was established pursuant to the "Rules of Information Strategy Committee," and is chaired by the Chief Digital Information Officer (CDIO). The Information Strategy Committee met nine times in the fiscal year ended March 2025. The Committee monitored the progress of the "DX Comprehensive Strategy" formulated in the year ended March 31, 2021, which consists of DX Business Strategy, Data Driven (DD) Management Strategy, and DX HR Strategy, and discussed various initiatives such as the 'Digital Ground Design' which materialize the ideal state of our systems for a global group, the policy of cybersecurity strategy/structure expansion/inspection/training to respond to cyberattack, updating our global network, policies on next-generation human resources systems, internal agile software development, utilization of generative AIs, IT/DX R&D and the Strategic DX Support Program.
Under the system centered around the Information Strategy Committee, we are enhancing the system of internal control including management of various possible risks such as information leakage and cyberattacks through maintenance of the following rules, necessary in light of development and operation of information systems and information security.
- "Rules on Information System Management": rules on the process of procurement, introduction and operation of Information assets
- "Rules on IT Security": code of conduct for the system supervisory divisions regarding IT security
- "Rules on Information Management": basic policies in terms of information risk management system and information management
- "Rules on Protection of Personal Information": rules for the handling of personal information required for business execution (Applied only in Japan)
- "Rules on Cybersecurity Countermeasures": rules for preventive measures against cyberattacks and emergency countermeasures in the event of incident
- "Mitsui & Co. Group Cybersecurity Standards": basic cybersecurity measures aimed at being implemented in common across Mitsui Group companies
Furthermore, the importance of cybersecurity measures in the global group is increasing as cyberattacks occurring day to day become more sophisticated, advanced and severe, such as targeted attacks targeting specific companies and organizations, ransomware (encrypting files and demanding ransom in exchange for their decryption), BEC (Business Email Compromise), and indiscriminate email attacks that aimed at unspecified targets, and once a year, a report is made to the Board of Directors after deliberation in the Information Strategy Committee and the Executive Committee.
| Officer in charge | Representative Director, Senior Executive Managing Officer/Chief Digital Information Officer (CDIO)/Chairperson of Information Strategy Committee |
|---|---|
| Deliberative body | Information Strategy Committee |
| Department in Charge | Integrated Digital Strategy Div. |
Risk Management
The Mitsui has established an integrated risk management system that has centralized control over company-wide risks in the global group. The Corporate Staff Divisions, which act as the secretariat, manage risks from a company-wide perspective in the system.
Risk related to information systems and information security is positioned as an important risk in the integrated risk, and the following steps are taken.
- We establish relevant rules for safety of information systems and strengthening information security, appropriately ensure the confidentiality, integrity and availability of information and information systems owned by Mitsui and its subsidiaries, and manage risks such as information leaks by continuously indicating guidelines for improving the level of risk management.
- We have established the "Mitsui & Co. Group Cybersecurity Standards" to be followed by Group companies to strengthen cybersecurity measures in the global group. Furthermore, a "Cybersecurity Baseline Survey" is conducted once per year in each affiliate to self-assess the state of compliance with the standards and third-party evaluation is also performed through a "Cybersecurity Assessment".
- Mitsui has formulated response policies to security incidents in advance according to the scale and severity of damage as a cyber BCP (business continuity plan).
Protecting Personal Information
We have appointed a Chief Managing Officer of the Personal Information Protection Management System (PMS) and established a PMS office to work at heightening awareness among all management and staff of the importance of personal information protection, in accordance with the Personal Information Protection Guidelines and Rules on the Protection of Personal Information. As we have a broad spectrum of involvement in diverse commodities and services, we handle a large amount of personal information, particularly in B2C (business-to-consumer) business fields. Accordingly, we take particular care to ensure that all data is protected. From the perspective of accident prevention, in addition to our education and training systems, we appoint a Personal Information Management Officer in each division. These officers regularly review the status of personal information management in the daily course of business and enhance it as needed. Regarding compliance with the EU GDPR (General Data Protection Regulation) that came into effect in May 2018, Mitsui has established internal rules to ensure proper management systems and operational rules for the handling of personal data that falls within the scope of application of the GDPR at each Business Unit. Furthermore, we have provided all officers and employees with information on the GDPR via the intranet, and have been engaging in operational management required by the GDPR such as compliance with the duty of keeping records of information processing activities. We recognize that a timely response according to global standards towards other overseas laws and regulations related to personal information, in addition to the GDPR, leads to the enhancement of our corporate value.
Initiatives
The Company formulated the Mitsui Cybersecurity Strategy in the fiscal year ended March 31, 2025, and is strengthening cybersecurity measures as a global group based on the strategy while drawing upon the knowledge of Mitsui Bussan Secure Directions, which is a dedicated cybersecurity subsidiary, and MITSUI KNOWLEDGE INDUSTRY, which is an information systems subsidiary.
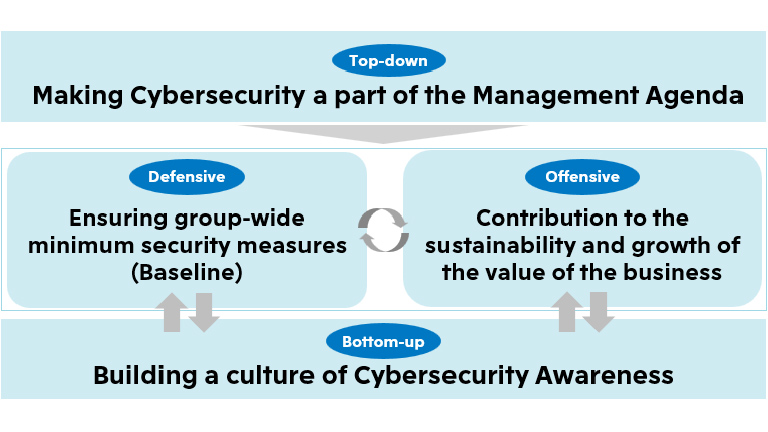
Making Cybersecurity a part of the Management Agenda
Cybersecurity measures are positioned as an important element of internal control, and are promoted as part of integrated risk management for the entire global group, involving management of especially affiliated companies. Specifically, reports are made and discussions are held in the Information Strategy Committee, the Executive Committee, and the Board of Directors once a year, and awareness-raising activities are conducted for the management of affiliated companies through annual briefings and workshops.
Ensuring group-wide minimum security measures (Baseline)
We are promoting the establishment and optimization of a baseline for cybersecurity across the entire global group. Specifically, we drafts and executes measures in accordance with the cybersecurity framework of the National Institute of Standards and Technology of U.S., and takes measures separated into the three steps of "Hygiene", "Protection", and "Recovery" while utilizing the knowledge of Mitsui Bussan Secure Directions.
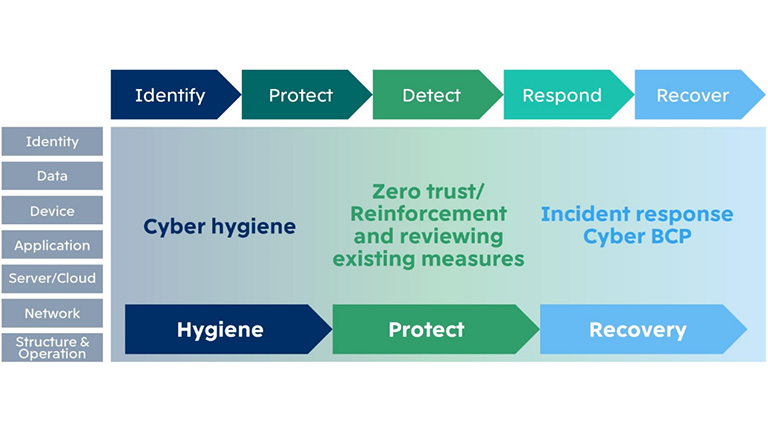
Hygiene
We believe in the importance of cyber hygiene, and engage in appropriate management of inventory for ascertaining the status of IT assets, and vulnerability management to determine and fix the cause of attacks as activities to maintain a healthy IT environment.
Protect
Based on the approach of "zero trust" (security measures that perform verification without trusting any access to information and systems to be protected regardless of whether inside or outside the network), we are strengthening security measures in various IT areas such as IDs, devices, data, network and the cloud. Furthermore, we are building, maintaining and expanding a system for around-the-clock global security monitoring and responding in the event of an incident.
Recovery
We have established the MBK-CSIRT (Computer Security Incident Response Team) as the center of security measures, working with cybersecurity leaders in each division to establish reporting and supporting systems, perform organized and continuous incident responses, and prevent recurrences. Furthermore, we have formulated response policies in the event of a security incident occurring according to the scale and severity of damage, and periodically conduct training to confirm effectiveness as needed.
Contribution to the sustainability and growth of the value of the business
We are actively enhancing our competitiveness and increasing added value by providing proactive, tailored support for cybersecurity measures related to our digital transformation (DX) initiatives. Specifically, we have established a dedicated consultation desk for security matters pertaining to DX projects, thereby offering advisory and support services from the project formation stage in accordance with the principles of "Security by Design." In response to the rapid advancement of generative AI technologies, we are promoting the utilization of such technologies to improve productivity and enhance business value across the Company. In the current fiscal year, we have commenced the use of Microsoft 365 Copilot as a company-wide AI platform. Furthermore, we are advancing multiple generative AI projects tailored to specific operations and business domains. To ensure the secure use of generative AI, we have implemented a range of risk mitigation measures. These include a comprehensive review of access rights to internal data, the formulation of risk guidelines for the use and provision of generative AI, and the mandatory completion of e-learning programs outlining key precautions for AI usage. Additionally, when employees seek to use generative AI tools that fall outside the Company's standard offerings, a formal application process is required. In such cases, we recommend the use of AI models that do not engage in retraining based on input data and that are not subject to monitoring of input/output data by service providers. Through these initiatives, we are contributing to the safe and effective utilization of digital transformation and generative AI technologies across Mitsui & Co. Group.
Building a culture of Cybersecurity Awareness
We are promoting the creation of a culture and atmosphere where security measures are considered "common sense" through education and awareness-raising for each level and role. Specifically, we have launched a "Cybersecurity Portal" for officers and employees including those of affiliates for the purpose of raising cybersecurity awareness and preventing the spread of damage from cyberattacks, and provide them with a variety of information such as the latest trends, case studies and appropriate actions and measures against cyberattacks to be taken by officers and employees. In addition, we prepare and utilize "Cybersecurity e-Learning" for end-users and security personnel respectively.